Introduction — Governance Is Risk Management in Disguise
The biggest risks aren’t the ones that explode — they’re the ones that quietly go ungoverned.
When risk strikes, it rarely shows up as a dramatic collapse. More often, it creeps in through misalignment, indecision, and blind spots. A breached endpoint here, a failed project there. Missed escalations. Overlooked trade-offs. Critical controls bypassed in the name of speed. By the time headlines are made, the risk isn’t new — it’s just become undeniable.
IT governance, done well, catches these moments before they metastasize. Not by adding red tape, but by wiring risk awareness into the decisions that matter — who makes them, how they’re made, and what gets surfaced before it’s too late.
And yet, too many organizations treat risk management as a parallel universe — a siloed function, downstream of strategy and separate from delivery. The result? CIOs chasing risk after it materializes, compliance teams playing whack-a-mole, and business leaders asking why no one raised the flag sooner.
The data tells the story: large IT projects exceed their budgets by an average of 45%, deliver 56% less value than forecast, and are 7% more likely to run over schedule, according to McKinsey. Meanwhile, IBM’s 2023 report puts the average cost of a data breach at $4.45 million — the highest ever recorded. These aren’t just technical failures. They’re governance failures. And they start with risk decisions that were never governed at all.
This article is about closing that gap — not by layering on more controls, but by rethinking governance as a strategic system of risk intelligence. One that sees risk not as an obstacle, but as a signal — embedded into architecture reviews, portfolio discussions, and boardroom dashboards.
We’ll explore:
- Why traditional risk management models are no longer enough
- The specific types of risk IT governance must make visible
- The structures and mechanisms that prevent failure before it happens
- How CIOs and IT leaders can lead with resilience — not just control
Every IT decision is a risk decision — and governance is the system that makes those risks visible, accountable, and aligned with strategy. The cost of ignoring this isn’t theoretical. It’s measured in breached systems, wasted investments, and eroded trust.
For organizations navigating tight regulatory environments, see our companion piece: Compliance in IT Governance: Turning Regulations into Actionable Controls.
Why Risk Must Be Embedded in IT Governance
Risk is not a background process. It’s a condition of every decision made in technology — from how systems are architected, to which vendors are selected, to how fast features go live.
Yet many organizations still treat IT risk management as an adjacent process, managed by separate teams and activated too late. Governance decides the roadmap. Risk comes in after the wheels are turning. The result? A façade of control that fractures under pressure.
Risk doesn’t live in a spreadsheet, a department, or a quarterly review cycle — and pretending it does is how governance fails.
Technology today doesn’t just support business strategy; it is the strategy. IT systems handle customer interactions, financial operations, product delivery, and regulatory compliance — often simultaneously. Decisions made at the portfolio level can ripple downstream into regulatory exposure, security vulnerabilities, or reputational harm. And when those decisions are made without an integrated view of risk, governance loses its grip.
From Reactive Risk to Strategic Risk Governance
Traditional risk management asks, “Are we compliant?” Strategic governance asks, “Are we making decisions that align with our risk appetite and business goals?” That difference isn’t just semantic. It’s structural.
Here’s how the shift plays out:
Legacy vs. Integrated Model
| Legacy Model | Integrated Governance Model |
| Risk reviewed after strategy is set | Risk integrated into strategic planning |
| Risk teams assess controls | Governance bodies assess risk-based trade-offs |
| Compliance is the dominant concern | Enterprise value and risk tolerance are balanced |
| Escalation happens after red flags | Escalation paths are defined upfront |
Embedding risk in governance isn’t about slowing decisions. It’s about making them intentionally — with a clear view of what’s at stake, who owns the risk, and how trade-offs will be managed.
Consider the difference between a project that launches without risk review, and one that builds governance into its architecture. In the former, risk is discovered in production. In the latter, it’s designed out in the early stages or at least acknowledged and accepted — not ignored.
That’s not bureaucracy. That’s operational maturity.
Risk isn’t a separate track — it’s the terrain. Governance that treats risk as an afterthought invites failure. To build resilience, embed risk thinking into the very architecture of decision-making — not as a gatekeeper, but as a compass.
Core IT Risk Domains Managed Through Governance
You don’t manage risk in the abstract. You manage it where it lives — in systems, decisions, trade-offs, and behaviors. That’s why effective governance doesn’t just define structures. It identifies where risk hides, how it materializes, and who has the authority to act before it escalates.
Enterprise IT doesn’t face a single kind of risk. It navigates multiple risk domains at once — often interconnected, and often moving faster than formal review cycles can keep up. That’s where governance comes in: not to eliminate uncertainty, but to give it shape, ownership, and a path to resolution.
Below are four risk domains where IT governance must play an active, deliberate role:
Cybersecurity and Information Risk
Security isn’t just a technical discipline — it’s a governance imperative. With attack surfaces expanding and threat actors growing more sophisticated, the board is no longer asking, “Are we secure?” They’re asking, “How are we governing security risk?”
Governance responsibilities here include:
- Defining enterprise-wide risk thresholds for cybersecurity (e.g., what level of vulnerability is tolerable?)
- Prioritizing security investments through steering committees and portfolio governance
- Overseeing incident preparedness via escalation pathways, tabletop exercises, and resilience metrics
- Establishing board-level visibility, often in partnership with CISOs and risk officers, to track key indicators
When governance fails in this domain, the cost isn’t just financial — it’s existential. Reputational damage, customer churn, and legal liability often follow closely behind technical compromise.
Operational and Technology Risk
The complexity of modern IT systems creates fertile ground for failure — outages, integration breakdowns, legacy fragility, or technical debt that quietly compounds until it becomes a crisis.
Effective governance mitigates these risks by:
- Embedding architecture review boards into the project lifecycle
- Enforcing change management discipline that includes risk evaluation, not just schedule impact
- Surfacing interdependencies through portfolio governance to detect cascade failure potential
- Ensuring business continuity planning isn’t a checkbox, but a program linked to real operational scenarios
When decisions are made without visibility into these structural risks, organizations end up with brittle infrastructure disguised as innovation.
Strategic and Financial Risk
Not all risks come from security flaws or system outages. Some come from the decisions we fund — or fail to fund. Misaligned investments, sunk costs in dead-end platforms, or digital projects that duplicate rather than integrate are all symptoms of weak strategic governance.
Governance must:
- Connect project approval to business value and risk appetite
- Prevent project sprawl by using value gates and strategic filtering
- Track benefits realization to ensure that risk-adjusted ROI is measured, not assumed
- Intervene when costs spiral or when risks to outcomes outweigh potential returns
Without strong governance here, organizations lose not just money — they lose momentum.
Reputational Risk
Sometimes, the greatest risk is perception. A data breach. A failed product launch. An ethics scandal involving AI or automation. These events may begin in IT, but their damage is corporate.
IT governance plays a critical role in reputational defense by:
- Elevating controversial or high-impact decisions to executive forums
- Ensuring ethics and risk are reviewed together, not separately
- Designing transparent escalation paths that make risk visible before it becomes public
- Embedding crisis response roles into governance charters, so decision-making doesn’t stall under pressure
Reputation isn’t something you can ensure after the fact. It’s something you protect through foresight, structure, and disciplined governance.
Enterprise risk doesn’t come in one flavor — and neither should governance. From security and infrastructure to investment and reputation, every major risk domain must be actively governed, not just monitored. The goal isn’t to eliminate risk. It’s to own it — visibly, strategically, and before it owns you.
Emerging Risk Domains That Governance Can’t Ignore
Most governance models are built to manage the familiar: cybersecurity, operational continuity, regulatory compliance. But the landscape is shifting — and so are the exposures. Risks that once lived on the edge of the enterprise are now embedded deep within its digital DNA.
As technology evolves, so must governance. The structures that oversee today’s core IT operations must now expand to address tomorrow’s blind spots — not reactively, but by design.
Let’s discuss four domains where risk is rising faster than governance frameworks are adapting:
AI-Driven Decision-Making
Machine learning is already making real-time decisions in fraud detection, customer service, and predictive analytics — often without a human in the loop. Yet many governance bodies have no formal process for:
- Auditing AI model logic or bias
- Documenting accountability for outcomes
- Setting thresholds for explainability and intervention
Governance must shift from asking “Did we buy the right tool?” to “Do we understand what the tool is learning, and who owns the risk when it learns wrong?”
ESG and Sustainability Risk
Environmental, Social, and Governance (ESG) reporting is no longer an investor checkbox — it’s a strategic lens shaping enterprise behavior. But most IT governance models don’t track:
- Carbon impact of cloud operations
- Digital accessibility and inclusion risks
- Social consequences of automation at scale
As ESG becomes a board-level priority, governance must expand beyond efficiency and resilience — and into ethics and sustainability.
Data Sovereignty in Cross-Border Ecosystems
Cloud-first architectures and multi-region deployments bring new complexities around data jurisdiction, residency, and localization laws. What begins as a storage decision can trigger:
- Legal and regulatory risk
- Third-party exposure across borders
- Conflict between innovation and compliance
Governance must have built-in mechanisms to flag and escalate sovereignty concerns — before they cross legal boundaries.
Low-Code / No-Code and Platform Governance
As business units adopt internal platforms and no-code solutions, risk becomes decentralized:
- Shadow IT proliferates
- Compliance checks are bypassed
- Critical workflows are built outside traditional SDLCs
The solution isn’t to block these tools — it’s to govern them differently. That means embedding governance into platform configuration, permission models, and portfolio visibility.
Traditional risk domains aren’t going away — but they’re no longer the full picture. If governance is going to scale with digital complexity, it needs to project forward — not just control backward. That means extending visibility, structure, and decision rights into places risk is now hiding – in models, platforms, ecosystems, and ethics.
Governance Structures That Operationalize Risk Thinking
Risk isn’t managed through intent — it’s managed through structure. Even the most sophisticated risk frameworks fall apart if no one is assigned ownership, no one knows when to escalate, and no one has the mandate to say “stop” or “not yet.”
This is where IT governance proves its value: not as a bureaucratic overlay, but as a system of connected forums where decisions are made, risks are surfaced, and accountability is enforced. If governance defines how decisions happen, then these structures define where they happen — and who’s in the room when they do.
The goal isn’t to create more meetings. It’s to create the right ones, with the right stakeholders, at the right altitude of risk.
Here’s how key governance structures activate risk management across the enterprise:
IT Steering Committees
- Focus: Strategic alignment, investment decisions, portfolio risk
- Risk Role:
- Assess risk exposure at the portfolio level
- Filter out initiatives misaligned with risk appetite
- Track cumulative delivery risk (schedule compression, resource contention)
- Best Practice: Include risk officers and business sponsors — not just IT leaders — to ensure enterprise-level trade-offs are visible and debated.
Enterprise Architecture Boards
- Focus: Systems architecture, integration, technology strategy
- Risk Role:
- Identify architectural fragility and interdependencies
- Evaluate technical debt and sustainability risk
- Approve or reject proposed solutions based on risk-informed design
- Best Practice: Link architecture decisions explicitly to resilience goals — not just performance or cost efficiency.
Program and Project Governance Forums
- Focus: Initiative-level performance, scope, and delivery control
- Risk Role:
- Ensure project-level risks are identified, documented, and escalated
- Track risk-adjusted value and delivery confidence
- Monitor emerging risks (vendor delays, capability gaps, data risks)
- Best Practice: Require active risk logs and periodic risk reviews as standard governance artifacts.
Security and Risk Committees (or Risk Councils)
- Focus: Enterprise risk oversight and cybersecurity posture
- Risk Role:
- Aggregate and prioritize systemic risk
- Bridge IT risk with enterprise risk management (ERM) functions
- Recommend policy changes or escalation paths based on threat landscape
- Best Practice: Avoid separating “technical” risk from “business” risk — both must inform governance decisions.
Board-Level Oversight Structures
- Focus: Strategic risk, reputational exposure, regulatory accountability
- Risk Role:
- Review key risk indicators (KRIs) tied to IT operations
- Oversee risk posture in emerging areas like AI, data governance, and cloud dependency
- Serve as the final escalation point for enterprise-level risk decisions
- Best Practice: Ensure that risk metrics presented to the board are actionable, not just descriptive.
Organizational Diagram / Matrix
| Governance Structure | Level | Primary Risk Function |
| IT Steering Committee | Exec | Portfolio risk, investment alignment |
| EA Review Board | Tactical | Architectural fragility, dependencies |
| Project/Program Governance | Operational | Delivery risk, controls enforcement |
| Risk or Security Committee | Strategic | Systemic risk, risk aggregation |
| Board Oversight | Board | Regulatory/reputational risk review |
Governance structures aren’t just decision-making bodies — they’re risk sensors. When designed intentionally, they form a network of accountability that sees risk early, surfaces it quickly, and responds strategically. Without them, risk doesn’t just rise — it disappears until it’s too late.
Governance Mechanisms That Support Risk Mitigation
Structures define authority — but mechanisms define impact.
A well-designed IT governance model doesn’t just assign roles and create committees. It embeds risk thinking into the mechanisms that shape everyday decisions. These mechanisms aren’t abstract. They’re embedded into approvals, reviews, evaluations, and checkpoints that determine what moves forward, what gets paused, and what never makes it off the whiteboard.
The difference between a governance model that mitigates risk and one that merely observes it lies in these levers — in how they filter noise, elevate signals, and guide decisions under pressure.
Here are five essential governance mechanisms that operationalize risk mitigation across the enterprise:
Value Gates
Purpose: Govern which initiatives receive funding, resourcing, or progression through stages.
Risk Role:
- Filter out low-value, high-risk initiatives before they absorb time and budget
- Align project selection with strategic goals and risk tolerance
- Enforce non-negotiables (e.g., no funding without risk assessment, architecture review, or compliance validation)
Strategic Benefit:
Avoids wasteful investment and ensures risk trade-offs are made before execution begins.
Architecture Reviews
Purpose: Evaluate the design and integrity of proposed technology solutions.
Risk Role:
- Identify technical debt, complexity, or fragility early in solution design
- Prevent integration risks, performance bottlenecks, or vendor lock-in
- Assess alignment with enterprise architecture and resilience standards
Strategic Benefit:
Turns architecture into a line of defense against unscalable or brittle solutions.
Portfolio Reviews
Purpose: Assess health, risk, and value across all active IT programs and projects.
Risk Role:
- Reveal cumulative risk across initiatives (e.g., overlapping dependencies, schedule compression)
- Provide early visibility into delivery delays, resourcing conflicts, or scope creep
- Surface projects that no longer justify continued investment or carry excessive risk
Strategic Benefit:
Protects against systemic failure and strengthens cross-initiative coordination.
Risk-Adjusted Benefits Tracking
Purpose: Ensure benefit realization is measured against actual risk exposure and mitigation efforts.
Risk Role:
- Track value erosion due to unmanaged risk (e.g., delayed launch, rework, controls not met)
- Adjust ROI projections based on emerging threats or compliance requirements
- Reassess initiative priority as risks change over time
Strategic Benefit:
Connects business value with real-world risk realities — not just optimistic forecasts.
Scenario Planning and Stress Testing
Purpose: Anticipate how systems, teams, or initiatives perform under extreme or adverse conditions.
Risk Role:
- Simulate failure modes, cascading impacts, or stress events
- Identify under-tested assumptions and resilience gaps
- Inform escalation thresholds and recovery paths
Strategic Benefit:
Transforms uncertainty into preparation — and reactive governance into proactive readiness.
Mechanisms-to-Risk Table
| Value Gate | Filter high-risk, low-return initiatives |
| Architecture Reviews | Detect technical fragility, reduce complexity |
| Portfolio Reviews | Reveal interdependencies, resourcing gaps |
| Risk-Adjusted Benefits | Prevent overestimated ROI |
| Scenario Planning | Prepare for plausible failures |
Risk mitigation isn’t passive. It’s designed. Governance mechanisms are the levers that shape decisions, challenge assumptions, and convert strategy into resilience. When used with discipline, they don’t slow the business down — they keep it standing when pressure hits.
Risk Appetite, Escalation, and Decision Rights
Governance without thresholds is just conversation. And risk without ownership is just hope.
Every organization has a tolerance for risk — whether explicit or not. The question is whether that tolerance is defined, understood, and enforced through the governance model. Without that clarity, risk decisions devolve into improvisation: developers deciding when to skip a control, project teams pushing forward despite legal concerns, or infrastructure leads assuming it’s “probably fine.”
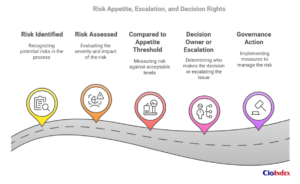
Governance exists to prevent that drift. It defines:
- Who owns which risks
- What levels of risk are tolerable
- When escalation is required
- Where trade-offs must be surfaced and approved
Without this scaffolding, organizations don’t just move fast — they move blind.
Defining Risk Appetite
Risk appetite isn’t about eliminating risk. It’s about articulating how much risk is acceptable in pursuit of value — and under what conditions. Governance plays a critical role in:
- Translating enterprise-level risk appetite into actionable IT decision frameworks
- Embedding those thresholds into policies, project approval criteria, and investment gating
- Creating differentiation between low, medium, and high-risk decisions — and who signs off on each
When appetite isn’t clearly defined, risk defaults to individual judgment. And individual judgment, no matter how well-intentioned, isn’t scalable.
Escalation Paths: Knowing When to Surface Risk
Escalation shouldn’t be ad hoc, or personality driven. Governance models must define:
- Triggers for escalation (e.g., material data risk, failure to meet control requirements, security exceptions)
- Escalation paths — who reviews what, and at which level (project board, steering committee, executive leadership, board of directors)
- Timeframes for escalation responses, particularly in fast-moving environments like Agile or crisis response
When escalation is undefined, risk stays buried until it becomes impact.
Clarifying Decision Rights
Perhaps the most overlooked — and most critical — governance control is decision rights: who can say yes, who must say no, and under what conditions a decision is valid.
Strong governance charters answer questions like:
- Can a project team override an architecture rejection?
- Who approves exceptions to policy or control gaps?
- What happens when risk and reward are in conflict — and who arbitrates that trade-off?
Without defined decision rights, risk isn’t governed — it’s negotiated.
Governance must define who owns different categories of risk, what thresholds trigger escalation, and where trade-offs occur (e.g., speed vs. control).
To ensure consistency and accountability in how risks are elevated, organizations can adopt the C.L.E.A.R.™ Escalation Model — a structured five-step framework that turns risk ambiguity into governance action.
C.L.E.A.R. stands for Context, Level, Escalation Threshold, Accountability, and Response Path — a process that helps teams surface the right risks, involve the right decision-makers, and route decisions through the right governance bodies.
This model brings rigor to decisions like:
- Should we accelerate go-live despite incomplete testing?
- Is a regulatory exception acceptable at the program level, or does it require board input?
The C.L.E.A.R.™ model ensures escalation isn’t emotional or inconsistent — it’s embedded in how governance makes trade-offs visible, defensible, and strategic.
The C.L.E.A.R.™ Escalation Model for IT Governance
| Letter | Component | Description |
| C | Context | Understand the business, technical, and regulatory context of the risk. |
| L | Level | Determine the severity and impact tier (project, program, portfolio, enterprise). |
| E | Escalation Threshold | Compare the risk to documented thresholds or appetite triggers. |
| A | Accountability | Identify the owner of the decision and who must be involved or informed. |
| R | Response Path | Activate the appropriate governance structure (e.g., Steering Committee, Board, EA Review) and document the outcome. |
To see how the C.L.E.A.R.™ model operates in practice, consider this example from a real-world cloud migration decision:
Case: Escalating a Cloud Migration Risk
The Cloud Decision No One Wanted to Own
A digital services team at a multinational retailer was preparing to migrate customer analytics from an on-prem data warehouse to a third-party cloud platform. The move promised faster insights and cost savings — but legal flagged potential data sovereignty issues due to cross-border processing in non-EU regions.
Delivery teams wanted to proceed. Legal advised caution. The CIO asked one question: “What’s our governance path for this?”
Using the C.L.E.A.R.™ model, the risk was evaluated:
- Context: Customer data in regulated markets (EU, UK)
- Level: Enterprise impact, touching both compliance and strategic analytics
- Escalation Threshold: Triggered due to GDPR exposure and conflicting policy interpretations
- Accountability: CIO and General Counsel jointly owned the risk decision
- Response Path: Escalated to the Data Governance Board → approved with additional contractual controls and a 90-day review clause
The project moved forward — with a paper trail, executive awareness, and mitigation aligned to risk appetite.
Without the model? That risk might’ve stayed in Slack channels until it became a regulatory investigation.
Risk governance isn’t just about process — it’s about power. Without clearly defined appetites, escalation paths, and decision rights, organizations leave risk in the hands of whoever speaks loudest or moves fastest. Governance ensures that risk decisions are made intentionally, transparently, and by the right people at the right time.
When Governance Fails to Manage Risk
Governance failures rarely look like dramatic moments in real time. More often, they unfold quietly — not with a bang, but with a series of silent omissions:
A skipped review.
A waived control.
A risk that “didn’t seem that serious at the time.”
It’s only when the breach happens, the regulator calls, or the project implodes that leaders realize the decisions leading to failure weren’t made recklessly — they simply weren’t governed.
Case: The Cost of Skipped Oversight
A large financial services provider launched a new mobile banking app on an accelerated timeline. The functionality was on point, the UX had been stress-tested, and stakeholders were eager to go live before quarter close.
But one piece of due diligence was skipped: a full legal review of data residency requirements for user accounts in international jurisdictions. A risk assessment had been drafted, but it never made it to the program governance forum. No one escalated it.
Months later, the company faced regulatory scrutiny in two countries. It didn’t matter that the feature worked. It mattered that no one had the authority, visibility, or process to stop and ask, should we ship this now?
The fine? Seven figures. The reputational damage? Harder to quantify.
The failure wasn’t technical. It was governance.
Symptoms of Weak Risk-Governance Integration
These failures don’t emerge from a single breakdown. They arise from patterns — subtle signals that governance is missing the mark:
Governance Bodies Without Risk Literacy
- Risk discussions are superficial, inconsistent, or overly dependent on one SME
- Cyber, operational, and strategic risk are treated as isolated conversations
Risk Registers Without Decision Pathways
- Risks are documented but never surfaced at the right forums
- No one knows when a “red” status means stop, adjust, or escalate
Trade-Offs Made Without Accountability
- Business teams push forward with risk-laden decisions in the name of speed
- No clear authority exists to enforce policy or delay rollout
Escalation Happens After the Damage
- Risk signals are raised — but too late, too informally, or to the wrong person
- The absence of defined thresholds allows risk to fester
Symptoms of Weak Governance
| Weakness | Manifestation |
| No risk literacy | Surface-level review, missing indicators |
| No decision thresholds | Delays, ambiguity, inconsistent response |
| No escalation clarity | Buried risks, avoidable crises |
| Project-level bias | Scope/cost dominate, risk is sidelined |
The Real Risk: Governance Drift
What’s most dangerous isn’t the absence of governance — it’s the illusion that it’s working.
When roles are unclear, meetings are pro forma, and controls are treated as optional, organizations believe they’re covered… right until they’re not. That drift is hard to detect, especially in fast-moving environments where velocity is rewarded more than visibility.
Risk doesn’t become a crisis by surprise — it becomes a crisis by neglect. Governance that lacks visibility, ownership, or authority isn’t just ineffective — it’s a liability. The cost of failed governance is never just operational. It’s strategic, financial, and reputational.
Measuring What Matters — Risk Metrics in IT Governance
Governance without metrics is governance without memory.
You can have the right forums, defined roles, escalation paths, and decision logs — but if no one is measuring what’s working and what’s failing, then governance becomes anecdotal. Ritual instead of strategy.
In the context of risk, this is more than a procedural flaw. It’s a visibility gap. Without metrics, risks aren’t just harder to manage — they’re harder to see. And that’s where governance fails, not because it’s absent, but because it’s operating in the dark.
Why Metrics Matter in Risk Governance
Metrics are the feedback loop of governance. They’re how CIOs, steering committees, and boards know:
- Which risks were caught
- Which ones weren’t
- How fast action was taken
- Where patterns of failure (or maturity) are forming
They bring objectivity to decision quality — helping organizations shift from “Are we following the process?” to “Is the process actually protecting us?”
If governance is how decisions are made — metrics are how those decisions are judged.
Types of Metrics That Matter
Not all metrics are equal. Some are predictive. Some are reflective. Some are noise disguised as insight. Strong governance focuses on a small set of leading and lagging indicators that signal whether risks are being identified, escalated, and resolved — or buried.
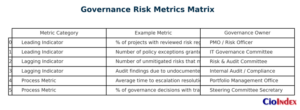
Leading Indicators
These measure risk visibility and readiness — warning signs that risk may be rising, or governance may be slipping:
- % of initiatives reviewed by an Architecture Board before launch
- % of in-flight projects with an up-to-date risk register
- Number of risks escalated vs. deferred or absorbed
- Frequency of policy exceptions granted outside approved thresholds
Lagging Indicators
These measure impact — events that indicate governance failed to intervene in time:
- Number of governance breakdowns cited in postmortems
- % of accepted risks that later materialized into incidents
- Regulatory findings tied to unreviewed decisions
- Cost impact of project or architectural rework due to ignored risk
Governance Process Metrics
These track governance performance itself — the velocity and integrity of decisions:
- Time from risk identification to escalation resolution
- Average time-to-decision by governance forum
- % of governance decisions backed by traceable documentation
What Metrics Should Avoid
Risk metrics can become dangerous when they signal the wrong things. Governance can’t be reduced to checkboxes and vanity dashboards.
- Avoid output-only metrics like “we reviewed 100% of projects” — that doesn’t tell you if the reviews caught anything.
- Avoid compliance-focused tunnel vision — metrics should measure effectiveness, not just adherence.
- Avoid overloading — governance teams can’t act on 40 KPIs. They need five that matter.
The best risk metrics answer one question: “Are we catching the right risks, at the right time, with the right response?”
Where Metrics Live in Governance
The best governance metrics aren’t buried in GRC dashboards or audit spreadsheets. They show up in the rooms where decisions are made — and they shape how those decisions are framed, challenged, and validated.
Where Metrics Show up in Governance
| Governance Forum | Key Risk Metric Use Cases |
| IT Steering Committee | % of portfolio flagged as high-risk; escalation response time |
| Architecture Review Board | % of proposals requiring exception; repeat exceptions granted |
| Portfolio Governance Office | Interdependencies flagged; cumulative portfolio risk exposure |
| Audit / Risk Committees | Risk acceptance trends; audit remediation velocity |
Metrics should not be trapped in dashboards — they should drive conversations.
These metrics shift governance from monitoring delivery to monitoring exposure. They don’t just say “we’re building” — they say, “we’re building with risk awareness.”
Embedding Metrics Into Governance Practice
Metrics can’t be an afterthought. They need to be:
- Built into governance charters and board agendas
- Tied to risk appetite thresholds (“if X happens → escalate to Y”)
- Owned by specific roles (e.g., PMO, EA lead, Risk Officer)
- Reviewed regularly and adjusted as blind spots emerge
They also need context. A spike in escalations might mean rising risk — or just better detection. That’s why metrics must be interpreted, not just reported.
If governance is the steering wheel, metrics are the windshield. Without them, organizations make risk decisions based on instinct, legacy patterns, or internal politics — not insight. With the right metrics in the right forums, governance becomes more than structure. It becomes intelligence. Adaptive. Defensible. And aligned to the very thing it’s meant to protect: enterprise value.
Risk-Governance Maturity Model
You don’t wake up with strong risk governance. It’s earned — through structure, iteration, and executive will. But unlike technical maturity, which can often be accelerated with the right tools or talent, risk governance maturity is cultural. It requires alignment, visibility, and most of all, clarity about who owns what risk and why.
Organizations often overestimate their maturity because they have risk processes on paper — or because they’ve “never had a major incident.” But maturity isn’t defined by absence of failure. It’s defined by preparedness, consistency, and decision quality under pressure.
The following model outlines four levels of risk-governance maturity, based on how integrated, strategic, and actionable the organization’s governance truly is.
Level 1: Ad Hoc
- Risk is discussed inconsistently, usually after incidents
- No formal connection between IT governance and risk management
- Decision-making is reactive and undocumented
- Escalation depends on personalities, not process
Indicator: Governance exists in name, but not in practice. Risk is invisible until it’s already impact.
Level 2: Defined
- Risk processes and governance forums exist, but operate in silos
- Risk registers are maintained, but not integrated into decision cycles
- Some escalation protocols exist, but ownership is unclear
- Governance reviews focus on delivery risk more than enterprise risk
Indicator: Governance can identify risk, but can’t yet prevent or control it.
Level 3: Integrated
- Risk is embedded into governance structures across architecture, portfolio, and project levels
- Risk appetite is defined and linked to decision-making thresholds
- Escalation paths are known and used proactively
- Scenario planning and risk-adjusted performance reviews are common
Indicator: Risk and governance are synchronized. Most risks are surfaced early and acted on with discipline.
Level 4: Strategic
- Risk governance is aligned to enterprise strategy and board oversight
- Decision rights, accountability, and risk appetite are fully operationalized
- Governance bodies use risk intelligence to shape priorities, not just defend against threats
- Culture promotes transparency, challenge, and informed trade-offs
Indicator: Risk is not just mitigated — it’s leveraged as a strategic input.
Risk governance maturity isn’t measured by how many risks you list — it’s measured by how consistently you act on them. Mature organizations embed risk into the rhythm of decision-making, treat governance as a living system, and evolve their structures to match the complexity of the enterprise.
The CIO as Strategic Risk Leader
Today’s CIO has two mandates: deliver the future, and de-risk the path to it. The role doesn’t just require technical fluency. It demands risk fluency. Anything less is a governance gap.
Because when governance fails, it doesn’t matter how well your tech stack performs — if the wrong risks aren’t surfaced, owned, or escalated, the entire operating model becomes fragile.
At this level, governance isn’t just a structure to be managed. It’s a platform for strategic influence. And no one is better positioned than the CIO to ensure that risk isn’t just reviewed — it’s understood, challenged, and acted upon.
The CIO as Risk Interpreter
Boards don’t need a technologist to explain how a firewall works. They need a translator who can explain what AI integration means for ethics, what cloud migration means for sovereignty, and what platform outage means for customer trust.
CIOs who lead through risk:
- Frame IT risks in business terms: revenue exposure, operational fragility, brand risk
- Surface trade-offs early: speed vs. assurance, innovation vs. control
- Align language across the C-suite: from engineers to auditors to the board
Risk decisions get made anyway. The CIO ensures they get made with clarity and consequence.
The CIO as Governance Integrator
Risk-aware governance is cross-functional by nature. It touches product, legal, finance, cyber, and compliance — and the CIO often sits at the crossroads of these worlds.
Leading CIOs actively:
- Partner with the CISO, CRO, CFO, and General Counsel to align risk and governance processes
- Sponsor governance structures that have teeth — not just templates
- Ensure that architecture boards, steering committees, and program forums are equipped to challenge assumptions, not just greenlight status updates
When governance is seen as “someone else’s job,” the CIO is the one who puts it back on the agenda.
The CIO as Cultural Catalyst
Governance isn’t only built through frameworks. It’s shaped through behavior.
CIOs influence the culture of risk by:
- Modeling transparency — admitting risk openly, not hiding it
- Rewarding constructive dissent — when teams challenge scope, speed, or security based on well-articulated risk
- Elevating maturity metrics — from KPIs to KRIs (Key Risk Indicators) to reinforce that value delivery isn’t separate from risk management
Culture change doesn’t start with a policy. It starts with leadership tone.
One way to embed that behavior is through structured tools like the C.L.E.A.R.™ Escalation Model (referenced above)— giving teams and governance forums a common language for identifying, evaluating, and acting on risk across all layers of the enterprise.
From Risk Aversion to Strategic Risk-Taking
There’s a difference between managing risk and avoiding it. Governance is about enabling calculated, strategic risks, the kind that leads to competitive advantage, not compliance paralysis.
CIOs must help their organizations:
- Understand which risks are worth taking — and why
- Build escalation frameworks that support speed with accountability
- Use risk appetite as a guide for innovation, not just a brake on progress
Governance isn’t the enemy of agility. Done right, it’s the architecture of confidence that lets you move fast — and recover faster.
CIOs don’t just manage systems — they manage risk. The most effective IT leaders shape governance not as a control function, but as a strategic enabler. When risk is surfaced early, owned clearly, and acted on decisively, the CIO isn’t just protecting the enterprise — they’re helping lead it forward.
Is Your Risk Governance Model Working? A Quick Self-Diagnostic
Governance isn’t just structure — it’s behavior at scale. And behavior is only visible when it’s tested. Before wrapping up, take five minutes to pressure-test your organization’s current approach to risk-aware IT governance.
Use the questions below to evaluate whether your model surfaces risk early, assigns it clearly, and routes it intentionally.
Risk Governance Self-Diagnostic: 5 Key Questions
- Ownership:
Does your governance model define who owns risk decisions at the project, program, and portfolio levels? - Escalation Triggers:
Are escalation thresholds or risk appetite breaches formally documented — and understood by delivery teams? - Governance Integration:
Is risk considered in steering committees, architecture boards, and portfolio reviews — or handled reactively? - Decision Records:
Are risk trade-offs, approvals, or mitigations traceable in decision logs or governance artifacts? - Leadership Visibility:
Does the CIO and executive leadership team regularly review risk posture across digital investments — not just audit findings?
Scoring Guidance
- 0–2 “Yes” answers: Your governance model is likely reactive. Risk decisions are being made — but not visibly or accountably.
- 3–4 “Yes” answers: You’re progressing toward integration. Risk is part of governance, but not consistently.
- 5 “Yes” answers: You’re operating in the strategic tier — where risk is surfaced, escalated, and acted on proactively.
You can’t govern risk if you can’t see it — or if no one owns it. This diagnostic isn’t about scorekeeping. It’s about surfacing the gaps that prevent governance from protecting what matters most: execution, trust, and resilience.
In Conclusion
The strongest organizations don’t eliminate risk — they govern it. Not through bureaucracy or backward-looking audits, but through structures that see risk early, assign it clearly, and act on it decisively.
This is what IT governance makes possible. Not a compliance layer. Not a reporting ritual. But a living system that defines how decisions are made, who owns the outcomes, and how risk is transformed from a liability into a leadership tool.
Every IT project, every cloud migration, every algorithm deployed carries implicit risk. The difference between fragility and resilience — between exposed and prepared — lies in whether that risk is surfaced before it becomes impact.
Throughout this article, we’ve explored how governance enables:
- Strategic alignment with enterprise risk appetite
- Integration of risk into architecture, project, and portfolio structures
- Defined escalation paths and decision rights when trade-offs are required
- CIO-led leadership that makes risk actionable, not avoidable
This isn’t a theory. It’s operational hygiene at scale. And it’s increasingly the difference between organizations that can move fast and those that can stay standing.
Because every IT decision is a risk decision — and governance is how you make that risk visible, intentional, and owned.
IT governance isn’t just how outcomes are enabled — it’s how they’re protected. The architecture of confidence isn’t built in code. It’s built in decisions. Governance ensures those decisions are made with discipline, accountability, and foresight.
For deeper insights and complete understanding check out our IT Governance Body of Knowledge available exclusively to our members.