Security as the New Enabler of Digital Transformation
Over the past decade, digital transformation has redefined how enterprises create value, compete, and grow. Cloud-native architectures, AI-driven decisioning, and data-powered ecosystems now form the operational backbone of modern business. As transformation accelerates, the very technologies that enable innovation also expand exposure—to disruption, data compromise, and reputational loss.
The implications are tangible and far-reaching. The MOVEit breach in 2023–2024 compromised more than 2,500 organizations worldwide, while the SolarWinds supply-chain attack revealed how even trusted partners can destabilize entire ecosystems. Each incident underscored a hard truth: transformation can advance only as far as its security foundations allow.
As explored in our earlier discussions on organizational resistance and cultural inertia, the most significant barriers to transformation are often internal, not technical. The same pattern holds true here: when cybersecurity is treated as an obstacle rather than an enabler, the organization undercuts its own progress.
Many enterprises still regard cybersecurity as a cost of doing business instead of a strategic investment in growth. In practice, security has become the infrastructure of trust—the invisible framework that sustains digital ecosystems across multi-cloud environments, AI pipelines, and extended partner networks. We discussed in our analysis of financial discipline and ROI, how organizations that embed security early achieve higher returns on digital initiatives and greater resilience under stress.
Recent Gartner research reinforces this shift. More than 70 percent of global executives now identify cybersecurity as the leading enabler of sustainable digital growth. For high-performing enterprises, it has evolved from a compliance function to a strategic capability that protects data integrity, accelerates innovation, and strengthens stakeholder confidence.
As digital risk converges with business risk—a theme we addressed when examining emerging operational and algorithmic threats – cybersecurity has moved from the server room to the boardroom. It is not the final layer of transformation but the first principle that determines whether transformation endures.
In this article, we examine how cybersecurity sustains digital transformation over the long term—serving as a strategic pillar, an integrated lifecycle discipline, and the cornerstone of enterprise trust.
The Cyber-Resilience Imperative in Digital Transformation
Every digital transformation carries within it a paradox: the more an enterprise digitizes, the more fragile its operations become. Cloud platforms, API-driven ecosystems, AI pipelines, and real-time data exchanges have multiplied both business capability and the number of potential failure points. In the past, resilience meant recovery; today, it means continuity under constant stress.
Cyber-resilience defines the enterprise’s ability to anticipate, withstand, and adapt to cyber incidents while maintaining essential operations. In an environment where disruption is continuous, resilience is not a contingency—it is a core design principle that determines whether digital transformation endures.
Modern transformation amplifies both reach and risk. Multi-cloud dependencies, globally distributed supply chains, and the proliferation of third-party integrations have created intricate webs of shared responsibility. The SolarWinds compromise showed how a single vulnerability in a trusted software update can ripple across thousands of organizations. The MOVEit exploitation revealed how weaknesses in third-party tools can trigger widespread exposure. These events did more than expose data; they undermined confidence in the very platforms that power digital innovation.
The lesson is clear: transformation cannot thrive atop instability. Fragmented security architectures, legacy dependencies, and inconsistent risk governance create fault lines that widen as digital initiatives scale. Supply-chain assurance and third-party governance are now board-level imperatives—not technical concerns delegated to IT.
Resilience also extends into new territory: AI and automation integrity. As automation and AI become embedded in core operations, safeguarding the integrity of algorithms and training data is now as critical as protecting networks and endpoints.
Leading organizations treat cyber-resilience as a dynamic capability rather than a compliance goal. Frameworks such as NIST’s Cybersecurity Framework 2.0 and ISO/IEC 27005 provide structure, but true maturity lies in integration—embedding resilience into operating models, culture, and governance. These enterprises view resilience not as insurance but as a continuity engine that preserves uptime, sustains trust, and enables innovation without hesitation.
Cyber-resilience is therefore not a static outcome; it is a living discipline. It transforms cybersecurity from a defensive posture into an adaptive system—one that absorbs disruption, learns from it, and emerges stronger. In a digital economy defined by perpetual change, resilience is not what follows transformation; it is what allows transformation to last.
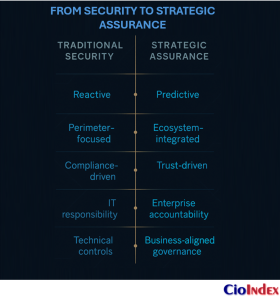
Cybersecurity as a Strategic Pillar — Not a Technical Add-On
Cybersecurity has long been viewed as a supporting function — a specialized discipline focused on perimeter defense, compliance checklists, and incident containment. That mindset no longer aligns with the reality of digital transformation. As enterprises shift from technology upgrades to full-scale reinvention, security must move from the periphery to the center of strategic decision-making.
This change reflects a structural truth: in a digitally driven enterprise, every business decision is a technology decision, and every technology decision carries security consequences. The boundary between IT risk and business risk has effectively disappeared. When a data breach can erode market capitalization, interrupt operations, or trigger regulatory penalties, security becomes inseparable from enterprise performance and reputation.
Executive leadership now treats cybersecurity as a fiduciary responsibility on par with financial oversight. Regulations have reinforced that expectation — from the SEC’s cyber disclosure requirements to the EU’s Digital Operational Resilience Act (DORA) and global data protection standards. Collectively, these frameworks elevate cybersecurity from a technical safeguard to an enterprise obligation, embedded in governance and accountability.
This shift has also redefined leadership dynamics. The relationship between the CIO and the CISO has evolved from coordination to co-ownership of digital risk. Instead of acting as operational silos, both functions now shape growth initiatives, calibrate risk appetite, and ensure that transformation objectives remain secure by design. Mature organizations measure success through shared outcomes: transformation initiatives delivered securely, downtime minimized, compliance sustained, and customer trust maintained.
Financial logic reinforces this shift. Viewing cybersecurity as an operational cost misses its strategic contribution to enterprise value. A resilient security posture reduces volatility, strengthens investor confidence, and accelerates recovery from disruption. In industries where trust is currency — finance, healthcare, critical infrastructure — security is no longer a defensive measure; it is a competitive signal of discipline, transparency, and reliability.
Embedding security into enterprise strategy transforms how transformation itself is governed. Discussions once centered on project delivery now focus on risk-adjusted outcomes. Cybersecurity considerations are built into portfolio management, ensuring that every initiative is evaluated not only for return but also for resilience. This integration extends from product innovation and customer experience to AI adoption and supply chain modernization.
Leading organizations formalize this philosophy through security by design and governance by intent. Security by design ensures that protection is architected into every platform, process, and decision from inception. Governance by intent aligns accountability and transparency, ensuring that cybersecurity investments directly support strategic priorities. Together, they define what digital maturity looks like in practice.
Cybersecurity, understood in this way, is not a defensive constraint or a technical control but a strategic pillar of enterprise leadership. It shapes trust, enables innovation, and safeguards continuity — the essential conditions for transformation to succeed and endure.
Embedding Cybersecurity into the Digital Transformation Lifecycle
Treating cybersecurity as strategy rather than infrastructure requires more than policy — it demands integration. Security must be designed into how the enterprise plans, builds, and evolves. When protection is aligned with value creation instead of applied as an afterthought, transformation gains momentum rather than friction.
The digital transformation lifecycle unfolds across five phases: strategy, architecture, execution, operations, and continuous improvement. Each phase carries unique opportunities to integrate resilience and trust.
1. Strategy: Aligning Security with Business Outcomes
Cybersecurity begins at the strategic level — with decisions about where and how the organization creates value. When risk discussions occur only after technology decisions, enterprises lose both agility and foresight.
Leading organizations incorporate security into their strategic vision, linking protection to growth objectives and risk appetite. They establish security-driven success metrics that connect cyber performance to business continuity, customer confidence, and regulatory assurance. The result is a security posture designed to enable, not constrain, innovation.
2. Architecture: Designing for Zero Trust and Data Integrity
Architecture translates strategy into structure. Zero trust principles — continuous verification, least-privilege access, and network segmentation — are built into the foundation, not layered on top.
Equally essential is the integration of privacy engineering and data governance. Data lineage, quality, and stewardship are treated as design assets. Security controls are embedded within APIs, analytics pipelines, and AI workflows, protecting not only systems but also the data and logic that power them.
3. Execution: Integrating DevSecOps and Continuous Validation
Transformation accelerates through agile and DevOps practices, but speed introduces risk if security is not embedded in delivery. DevSecOps closes that gap by making security part of the development DNA.
Automated testing, continuous vulnerability scanning, and real-time compliance validation ensure every release meets both innovation and protection thresholds. Some organizations now extend these capabilities through AI-assisted threat modeling, allowing them to anticipate risks as dynamically as they build.
4. Operations: From Protection to Intelligence
Once digital services go live, cybersecurity shifts from prevention to situational awareness. Continuous monitoring, threat intelligence, and red/blue team exercises reveal how the environment behaves under stress.
Resilient enterprises treat incidents as learning events. Post-event reviews inform architecture, playbooks, and governance, turning every disruption into an opportunity to strengthen continuity. This operational discipline transforms resilience from a slogan into a measurable competency.
5. Continuous Improvement: Building an Adaptive Security Culture
The lifecycle closes where it began — with leadership and learning. Continuous improvement is not just technical optimization but cultural evolution. Regular maturity assessments, scenario simulations, and threat landscape reviews ensure that security evolves with business priorities and emerging technologies. Increasingly, organizations extend this mindset into AI lifecycle security, protecting data pipelines and monitoring for model drift.
The most mature enterprises embed security conversations directly into management rhythms — board reviews, performance dashboards, and leadership dialogues — making resilience part of how the organization thinks and decides.
An Adaptive Loop, Not a Linear Path
The most effective organizations visualize the lifecycle as a closed feedback loop, not a sequence. Strategy shapes architecture, architecture informs execution, operations refine governance, and continuous improvement resets priorities. Security thus becomes both an input and an output of transformation.
This feedback-driven model converts cybersecurity from a control system into an operating system for digital trust — one that aligns protection with performance. It ensures that the mechanisms enabling innovation also sustain stability, turning speed into confidence and ambition into endurance.
Balancing Innovation and Risk — The Security–Agility Paradox
Digital transformation thrives on speed—but speed without discipline breeds fragility. Enterprises racing to innovate, deploy continuously, and respond instantly to market shifts often find themselves testing the limits of their own risk appetite. The paradox is clear: agility drives progress, yet without embedded security, it amplifies exposure.
For many organizations, this tension surfaces as a cultural divide. Product and innovation teams prioritize velocity; security teams emphasize assurance and control. Each is correct in purpose but incomplete in isolation. Innovation without protection undermines trust; protection without adaptability suppresses growth. The leadership challenge is not to choose between them, but to orchestrate both in harmony—achieving what can be called risk-informed velocity.
Reframing the Relationship Between Agility and Security
Mature enterprises no longer view security and agility as competing forces. Security provides the guardrails that make speed sustainable. Integrated practices such as DevSecOps and automated governance accelerate release cycles by embedding testing, compliance, and assurance directly into delivery pipelines.
Adaptive governance frameworks refine this further, calibrating oversight to context and risk. Critical systems and AI-driven decisions warrant stringent controls; low-impact experimentation can operate within lighter guardrails. This proportionality empowers innovation without compromising accountability.
Leadership and Culture as the Balancing Mechanism
Balancing innovation and risk begins with leadership. The CIO and CISO define not only the policies but the tone of collaboration. When both functions share accountability for transformation outcomes, agility and protection reinforce each other.
Culture makes the balance real. When teams perceive security as part of quality rather than external oversight, collaboration accelerates. Incentives shift from “fastest launch” to “most resilient delivery.” Open reporting and psychological safety allow teams to raise vulnerabilities early, strengthening both trust and performance.
Governance Built for Agility
Traditional governance relied on control through documentation and committees—effective in predictable environments, but misaligned with digital pace. Modern governance is lightweight, data-driven, and responsive. Policies are automated; risk thresholds are transparent; exceptions are guided by principles, not bureaucracy.
Real-time dashboards now integrate operational, compliance, and security indicators, allowing leadership to act on evidence rather than escalation. This model transforms governance from a checkpoint into a feedback system that learns as fast as it regulates. In AI-enabled environments, this adaptability is essential—risks evolve as quickly as the algorithms themselves.
Learning from Extremes
The cost of imbalance is well documented. Over-securing creates bottlenecks, deterring innovation and dulling competitive edge. Under-securing breeds vulnerability, eroding customer confidence and market trust.
Capital One’s experience illustrates both extremes. Rapid cloud adoption delivered agility and customer responsiveness but exposed configuration weaknesses that led to a major data breach. The company’s recovery—anchored in automation, zero-trust architecture, and cultural renewal—demonstrated that resilience and agility can coexist when governed by shared principles and accountability.
From Tension to Harmony
The balance between innovation and risk is not a static equilibrium but a living discipline that adjusts with context. In periods of rapid expansion, agility may take the lead; during volatility, resilience anchors stability. What matters is that both operate within a shared framework of trust, transparency, and feedback.
When leadership institutionalizes this rhythm, security becomes the confidence mechanism that enables bold innovation, while agility reinforces protection through continuous learning. The result is not compromise but convergence — a system in which speed and safety move together, sustained by trust.
The New Architecture of Trust
Every digital transformation ultimately competes on trust. Technology can be replicated, strategy can be emulated, and even data can be commoditized — but the credibility that binds customers, partners, and regulators to an enterprise cannot be copied. Trust has become the defining metric of the digital era: the factor that determines whether innovation endures or collapses under scrutiny.
Trust, however, is no longer an abstract virtue. It is a measurable, operational outcome shaped by how organizations secure data, respect privacy, demonstrate transparency, and recover from failure. Cybersecurity sits at the core of this architecture — not as a defensive wall, but as the connective tissue that sustains confidence across digital ecosystems.
From Security to Assurance
Traditional security models focused on protection; modern trust architectures focus on assurance — the ability to demonstrate integrity and accountability across every interaction. This shift reflects a broader evolution from control to credibility. Customers no longer ask whether systems are secure; they want to know whether the organization is trustworthy.
This distinction matters. Protection is invisible until it fails; assurance is visible because it is communicated. Enterprises that operationalize this principle publish transparency reports, disclose incident responses promptly, and integrate trust metrics into their annual statements. The message is clear: security is not secrecy — it is confidence earned through openness.
The Four Dimensions of Digital Trust
Modern enterprises build trust across four interconnected dimensions: integrity, reliability, privacy, and transparency.
- Integrity ensures that data, algorithms, and outcomes remain untampered — essential in an AI-driven world where manipulation can distort both analytics and ethics.
- Reliability reflects continuity and performance under stress; customers trust systems that endure.
- Privacy embodies respect for individuals and compliance with evolving regulations.
- Transparency translates these commitments into verifiable practice through communication, disclosure, and governance.
Together, these dimensions transform trust from sentiment into system design.
Identity and Data Confidence as Core Infrastructure
Across expanding digital ecosystems of partners, platforms, and autonomous systems, identity has become the new perimeter. Decentralized identity frameworks, blockchain-based attestations, and verifiable credentials now enable trust without constant verification.
Equally critical is data confidence — the assurance that information is authentic, accurate, and traceable. Organizations are investing in data provenance tools, integrity validation, and AI governance frameworks to ensure that trust scales alongside automation. The rise of self-sovereign identity (SSI) and zero-knowledge proofs further demonstrates how security innovation underpins privacy and autonomy simultaneously.
Trust as Competitive Advantage
For boards and investors, trust has become a quantifiable component of enterprise value. A strong trust posture attracts customers, strengthens brand equity, and reduces regulatory and reputational risk. Studies increasingly correlate high trust scores with superior market performance, lower cost of capital, and faster recovery after crises.
Enterprises that treat trust as strategic capital design governance to protect it. They integrate trust metrics into performance dashboards and link executive incentives to security, transparency, and ethical conduct. The trust narrative thus becomes both economic and moral — a source of differentiation that competitors cannot easily replicate.
Building the Architecture: From Policy to Practice
Creating a trust-centric enterprise requires coherence between principles, policy, and behavior. Board charters define intent, but culture defines execution. Transparent reporting, ethical AI frameworks, and privacy-by-design initiatives all contribute to this architecture.
The “new” in the new architecture of trust lies not in technology but in governance. Trust cannot be automated — it must be designed, communicated, and continually demonstrated. The organizations that succeed will be those that treat trust as infrastructure, not sentiment; as a measurable asset, not an aspiration.
Trust, Transformation, and the Future
As digital ecosystems become more interdependent, the architecture of trust becomes the architecture of the enterprise itself. In environments driven by AI, cloud interoperability, and global regulation, cybersecurity provides the scaffolding that keeps trust intact.
This redefinition of trust closes the loop begun by digital transformation: the same mechanisms that deliver speed, innovation, and connectivity must now deliver assurance, accountability, and transparency. The future belongs to organizations that understand this symmetry — where trust is not the byproduct of transformation, but its enduring purpose.
Cybersecurity Metrics That Matter for Digital Transformation
Transformation without measurement is aspiration without direction. Enterprises can only sustain what they can quantify, and nowhere is this more apparent than in cybersecurity. As digital ecosystems grow in complexity, leadership needs a language of measurement that links protection to performance, resilience to return, and trust to tangible value.
From Technical Indicators to Strategic Intelligence
Most organizations still evaluate cybersecurity through operational data — patch rates, incident counts, blocked intrusions, or vulnerability scans. While useful, these metrics measure activity, not assurance. They show motion, not maturity.
The real measure of cybersecurity in digital transformation is its impact on business continuity, resilience, and trust. Boards and executives require insight, not noise — metrics that translate security performance into enterprise outcomes.
The shift is therefore from technical indicators to strategic intelligence: understanding how security enables growth, reduces volatility, and reinforces stakeholder confidence. This requires reframing cybersecurity metrics around three leadership lenses — resilience, performance, and trust.
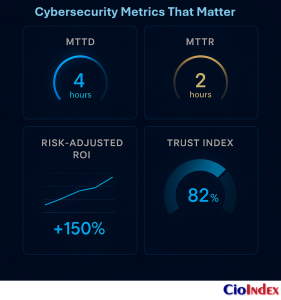
1. Measuring Resilience: How Fast Can We Absorb Shock?
Resilience metrics capture an enterprise’s ability to withstand and recover from disruption. They answer the board’s most important question: How prepared are we when—not if—a breach occurs?
Key indicators include:
- Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR) — the velocity of detection and containment.
- System recovery time — how long it takes to restore critical operations after an incident.
- Percentage of transformation initiatives with embedded security controls — a proxy for security integration maturity.
- Frequency and results of resilience exercises — measuring readiness, not just response.
These metrics link directly to operational confidence. A lower MTTR, for instance, is not only a security achievement but a competitive advantage: it minimizes downtime, protects brand credibility, and reduces financial exposure.
2. Measuring Performance: How Does Security Enable Strategy?
Performance-oriented metrics move the conversation from protection to value creation. They assess how effectively cybersecurity contributes to enterprise objectives — growth, efficiency, and innovation.
- Risk-adjusted ROI quantifies the financial return of transformation initiatives after accounting for potential cyber risk.
- Value at Risk (VaR) from cyber exposure expresses potential financial loss as a percentage of enterprise value.
- Cost avoidance and incident prevention savings demonstrate economic efficiency achieved through proactive controls.
- Security coverage of critical assets ensures that investment aligns with business impact, not technical convenience.
The goal is not to justify cybersecurity spend, but to demonstrate how it amplifies business performance — reducing uncertainty, protecting data-driven models, and sustaining operational integrity.
3. Measuring Trust: How Do Stakeholders Perceive Confidence?
Trust is the new currency of digital transformation — and it can be measured. Leading organizations are developing digital trust indices that quantify confidence across customers, partners, and regulators.
Indicative metrics include:
- Customer retention post-incident — a reflection of transparency and recovery effectiveness.
- Regulatory audit pass rates and compliance scores — the reliability of governance under scrutiny.
- Stakeholder trust surveys or sentiment analysis — qualitative validation of reputation resilience.
- Transparency maturity — measuring how openly and consistently the organization communicates about security and ethics.
Trust metrics bridge the human and operational dimensions of transformation. They show that cybersecurity is not only about defense but about credibility — a measurable source of enterprise stability.
Turning Metrics into Governance
The true value of cybersecurity metrics lies not in collection but in governance. Data without interpretation is noise; insight without accountability is risk. Mature enterprises integrate cybersecurity metrics into board dashboards and performance reviews, ensuring that risk and resilience are discussed with the same rigor as revenue and return.
Key success factors include:
- Single-source dashboards linking operational data to strategic indicators.
- Regular executive reviews that connect cyber performance to enterprise KPIs.
- Continuous recalibration — adapting thresholds as business models evolve and technologies mature.
Metrics, when integrated into decision-making, create a governance loop: measure, interpret, adjust, and improve. This turns cybersecurity from a compliance conversation into a continuous performance system.
The Leadership Imperative
Measuring cybersecurity effectively requires both precision and perspective. Too much detail overwhelms; too little context misleads. The challenge for leaders is to select the few metrics that drive the right behaviors — those that align protection with progress.
When boards see cybersecurity not as a technical report but as a strategic narrative expressed in data, transformation gains traction. Metrics become meaning; measurement becomes management.
Cybersecurity performance, in this light, is transformation performance — a direct reflection of how well the organization learns, adapts, and earns trust over time.
Leadership, Culture, and the Human Firewall
Technology can strengthen defenses, but people sustain them. Every strategy, architecture, and control ultimately depends on behavior — how decisions are made, how risks are understood, and how accountability is shared. In digital transformation, cybersecurity maturity reflects not only technical sophistication but the character of the organization itself.
Culture as the Operating System of Security
Breaches rarely occur because tools are missing; they happen when attention, communication, or ownership break down. Policies cannot compensate for a climate that normalizes risk indifference or isolates responsibility.
High-performing enterprises treat culture as the operating system of security. They embed shared norms: reporting a vulnerability is a strength, secure practices define quality, and vigilance is collective. This alignment translates directly into performance metrics — faster incident reporting, shorter response cycles, and stronger resilience over time.
Leadership as Cultural Architect
Leadership shapes how culture behaves under pressure. CIOs and CISOs act as architects of mindset, turning risk management into shared purpose. They communicate that security protects not only data but mission, reputation, and trust — reframing compliance as conviction.
Effective leaders demonstrate calm transparency during crises and reward proactive disclosure. They use stories and metrics together, connecting the “why” behind controls to the outcomes those controls enable. This narrative approach bridges technical and business teams, replacing enforcement with engagement.
Boards reinforce this dynamic through governance. Many now assess cultural indicators — participation in simulations, reporting cadence, employee trust surveys — alongside technical dashboards. Culture thus becomes a monitored asset, not an abstract virtue.
Psychological Safety and Responsible Behavior
True resilience requires an environment where people can speak before incidents become headlines. Fear silences; transparency teaches.
Enterprises with strong security climates encourage responsible disclosure, enabling employees and partners to report vulnerabilities without fear of reprisal. The model mirrors aviation’s “just culture,” treating errors as data to improve systems. The result is collective intelligence — a human network that senses risk faster than technology can.
Behavioral Cybersecurity: Understanding Human Risk
Humans are adaptive sensors, not weak links. Their decisions are influenced by incentives, workload, and context.
Leading organizations pair technical audits with behavioral risk assessments, examining communication gaps and cognitive biases that shape exposure. Training evolves into immersive simulation and AI-personalized learning, aligning content to roles and behaviors. The goal is durable habit change, not checklist compliance.
Embedding Security in Everyday Work
A mature security culture is invisible — it functions by instinct. Secure behavior becomes part of how work gets done rather than an added step.
Organizations that reach this level integrate security into onboarding, performance reviews, and leadership evaluations. They reinforce it through peer modeling, clear communication, and shared accountability. Culture spreads through demonstration, not directive. It extends beyond employees to vendors and partners, creating an ecosystem of aligned behavior.
From Awareness to Empowerment
Awareness informs; empowerment transforms. Empowerment gives people both the knowledge and authority to act. Developers secure code, marketing safeguards data, finance monitors access — each sees security as integral to results.
This distributed ownership forms the human firewall: adaptive, self-correcting, and collectively intelligent. It converts individual vigilance into organizational reflex.
Leadership’s Ultimate Measure
The maturity of a cybersecurity culture is revealed not by posters or training completion rates, but by conversations — how often leaders discuss risk in business meetings, how teams respond to incidents, and how openly lessons are shared.
When every person recognizes their role in resilience, security becomes identity, not obligation. It is this human architecture that distinguishes transformation that endures from transformation that merely changes. The following case studies illustrate what that looks like in practice.
Case Studies — Security-Enabled Transformation Success
Digital transformation is ultimately tested not by design, but by disruption. The most instructive examples come from organizations that turned crisis, scrutiny, or complexity into catalysts for deeper resilience and trust. Across industries, these cases reveal a common truth: enterprises that integrate cybersecurity early outperform those that treat it as a downstream safeguard.
Capital One — Cloud Innovation and the Governance Reset
When Capital One migrated core banking systems to the cloud, it became one of the first major financial institutions to embrace cloud-native architecture at scale. In 2019, a misconfigured firewall in its AWS environment exposed more than 100 million customer applications — a breach that drew global attention.
Instead of retreating, the bank treated the incident as a turning point. It overhauled its governance model, embedded security in its DevSecOps pipelines, and implemented automated compliance validation across every workload. Cultural transparency replaced blame; accountability was reframed as learning.
The outcome was transformation through maturity: accelerated deployment cycles with measurable risk reduction and a strengthened reputation for openness. Capital One’s evolution underscored that resilience is not the absence of failure, but the ability to rebuild stronger than before.
Maersk — The NotPetya Attack and the Anatomy of Recovery
In June 2017, the NotPetya malware attack crippled A.P. Møller–Maersk, halting shipping operations across 600 locations and rendering 45,000 PCs and 4,000 servers inoperable. Yet within ten days, the company restored global systems — a feat of resilience that became industry legend.
The recovery hinged on disciplined leadership and preparedness. A remote backup server in Ghana — almost by chance — became the anchor for restoration. In the aftermath, Maersk completely redesigned its cyber architecture, unifying IT and OT security, implementing zero trust principles, and establishing a cross-enterprise resilience governance framework.
The company’s transformation demonstrated that true maturity lies in the speed of recovery, not the illusion of invulnerability. Maersk’s post-crisis model now informs national and global supply-chain resilience strategies.
Colonial Pipeline — When Cyber Risk Became a National Event
In 2021, a ransomware attack on Colonial Pipeline disrupted nearly half of the U.S. East Coast’s fuel supply, igniting public panic and highlighting the systemic impact of a single compromise. The incident reframed cybersecurity as a matter of economic stability and national security.
Colonial’s response — rebuilding its operational technology network, instituting strict access segmentation, and collaborating with federal agencies — catalyzed sector-wide change. The event prompted new U.S. federal directives for pipeline operators and accelerated the national shift toward zero-trust architecture and real-time incident reporting.
Its enduring lesson: cybersecurity can no longer be confined to corporate governance; it is public infrastructure. Executive accountability and interagency coordination are now prerequisites for resilience at national scale.
Johnson & Johnson — Transparency as a Pillar of Digital Trust
In 2016, Johnson & Johnson took an unprecedented step: it publicly disclosed potential cybersecurity vulnerabilities in its connected insulin pumps. Rather than concealing the risk, the company used transparency as a foundation for trust.
J&J established a product cybersecurity governance board, implemented security-by-design principles across its medical device lifecycle, and created a coordinated disclosure process for researchers. This model became a benchmark for the industry and informed later FDA cybersecurity guidance.
The outcome was both reputational and operational. Patients remained confident, regulators commended openness, and competitors followed suit. J&J’s decision redefined the relationship between privacy, ethics, and digital health — proving that visibility, not secrecy, builds credibility.
Singapore — Building a Nation on Digital Trust
After a 2018 breach at SingHealth compromised 1.5 million citizen records, Singapore undertook one of the most comprehensive cybersecurity overhauls in the public sector. Under the Smart Nation and Digital Government initiative, it launched a National Cybersecurity Strategy, created the Cyber Security Agency of Singapore (CSA), and mandated secure-by-design standards for all ministries.
The transformation unified digital identity, privacy, and governance under a national Zero Trust framework. It also institutionalized mandatory incident reporting, cyber education across the civil service, and metrics to measure agency readiness.
Singapore, today, consistently ranks among the world’s top five cyber-resilient nations. Its model demonstrates how national trust architecture can align government, industry, and citizens around shared resilience.
Microsoft — Governance by Design in the Age of AI
In the early 2000s, Microsoft faced escalating security crises — from Code Red to SQL Slammer — that eroded trust in its products. In response, it created the Secure Development Lifecycle (SDL), embedding security into every stage of product design and release.
Over the years, SDL became a global benchmark adopted by governments and enterprises alike. Microsoft extended this model into its Responsible AI governance framework, applying similar principles of risk evaluation, transparency, and accountability to AI systems.
The result has been both strategic and cultural: a sustained increase in product reliability, regulatory trust, and customer confidence. Microsoft’s evolution illustrates that embedding governance in innovation processes turns security from a reaction into a core capability.
The Common Pattern — From Response to Reinvention
Across industries and sectors, these real-world cases share a single trajectory: each began with exposure and ended with reinvention.
- Capital One reframed compliance as innovation.
- Maersk turned recovery into institutional resilience.
- Colonial Pipeline transformed governance from corporate to national.
- Johnson & Johnson proved that transparency builds trust.
- Singapore embedded trust in national policy.
- Microsoft institutionalized governance as culture.
They demonstrate that the most successful digital transformations are not defined by the technologies adopted, but by how organizations learn, govern, and rebuild after disruption. Cybersecurity is the mechanism through which transformation endures — a discipline that turns crisis into capability.
The Strategic Imperative of Trust
The story of digital transformation is, at its core, a story of trust. Every breakthrough in technology, every leap in efficiency, every new digital ecosystem ultimately depends on whether stakeholders believe the enterprise can protect what matters most — data, identity, and integrity.
Cybersecurity has evolved far beyond control and compliance. It is now the invisible architecture of progress — the mechanism that makes speed sustainable, innovation credible, and transformation continuous. The organizations that lead in this new era are not those that move fastest, but those that move safely and transparently, bringing trust along with every change they make.
Over the past decade, the lesson has become unmistakable: digital transformation does not end with technology adoption; it matures through accountability. Governance, culture, and resilience are no longer supporting elements — they are the infrastructure of value creation itself.
Leaders who recognize this see cybersecurity not as a defensive shield, but as a strategic discipline of adaptation. It defines how enterprises evolve, how they learn from disruption, and how they build confidence in an age of uncertainty.
The next horizon — shaped by AI, automation, and global interdependence — will not reward velocity alone. It will reward organizations that can move fast without breaking trust. In that environment, cybersecurity becomes not a technical safeguard, but the ultimate measure of leadership maturity.
For digital leaders of today, five imperatives will define that maturity:
- Lead from the boardroom. Cyber risk is enterprise risk — governance must own it.
- Design for security, not around it. Embed protection into the lifecycle of transformation.
- Make trust measurable. Treat credibility as an asset, not an assumption.
- Empower the human firewall. Culture, not tools, determines resilience.
- Adapt continuously. Governance must evolve as fast as technology itself.
To lead in the digital future is to transform through trust — not once, but continuously, with integrity as the core operating principle.