IT Governance Knowledge – Page 58
Step into the CIO-Knowledgebase, your trusted guide in navigating the expansive domain of IT Management. With a repository encompassing over 650 topics, this learning and research tool is meticulously curated to support your professional growth and informed decision-making.
Discover a wealth of resources including documents, articles, whitepapers, and presentations, all aimed at equipping you with a robust understanding of leveraging IT for value. This CIO-Knowledgebase is an evolving entity, constantly updated with the latest insights to keep you informed in the dynamic IT landscape.
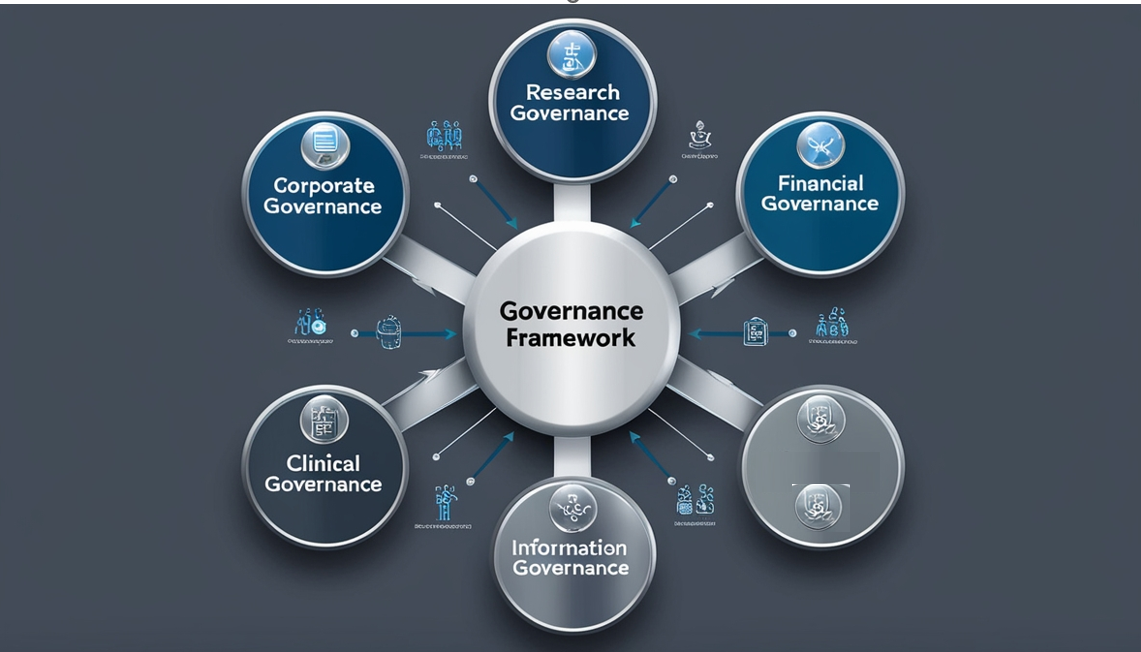
Our categorical hierarchy meticulously segments the vast field of IT management into seven core domains, reflecting the multifaceted responsibilities of a CIO.
The CIO Knowledgebase is a community-driven platform, fostering learning, sharing, and evolving together. Whether you are just embarking on your IT career or are a seasoned CIO, the plethora of resources available is tailored to meet your quest for knowledge and professional advancement. Your journey towards becoming an adept IT professional is well-supported here!
Featured Resources in: IT Governance Knowledge